Recently Facebook, Reddit, Google, LinkedIn, Microsoft, Twitter and YouTube committed to removing coronavirus-related misinformation from their platforms.
COVID-19 is being described as the first major pandemic of the social media age. In troubling times, social media helps distribute vital knowledge to the masses. Unfortunately, this comes with myriad misinformation, much of which is spread through social media bots.
These fake accounts are common on Twitter, Facebook, and Instagram. They have one goal: to spread fear and fake news.
We witnessed this in the 2016 United States presidential elections, with arson rumours in the bushfire crisis, and we're seeing it again in relation to the coronavirus pandemic.
Busy busting bots
The exact scale of misinformation is difficult to measure. But its global presence can be felt through snapshots of Twitter bot involvement in COVID-19-related hashtag activity.
Bot Sentinel is a website that uses machine learning to identify potential Twitter bots, using a score and rating. According to the site, on March 26 bot accounts were responsible for 828 counts of #coronavirus, 544 counts of #COVID19 and 255 counts of #Coronavirus hashtags within 24 hours.
These hashtags respectively took the 1st, 3rd and 7th positions of all top-trolled Twitter hashtags.
It's important to note the actual number of coronavirus-related bot tweets are likely much higher, as Bot Sentinel only recognises hashtag terms (such as #coronavirus), and wouldn't pick up on "coronavirus", "COVID19" or "Coronavirus".
How are bots created?
Bots are usually managed by automated programs called bot "campaigns", and these are controlled by human users.
The actual process of creating such a campaign is relatively simple. There are several websites that teach people how to do this for "marketing" purposes. In the underground hacker economy on the dark web, such services are available for hire.
While it's difficult to attribute bots to the humans controlling them, the purpose of bot campaigns is obvious: create social disorder by spreading misinformation. This can increase public anxiety, frustration and anger against authorities in certain situations.
A 2019 report published by researchers from the Oxford Internet Institute revealed a worrying trend in organised "social media manipulation by governments and political parties". They reported:
Evidence of organised social media manipulation campaigns which have taken place in 70 countries, up from 48 countries in 2018 and 28 countries in 2017. In each country, there is at least one political party or government agency using social media to shape public attitudes domestically.
The modus operandi of bots
Typically, in the context of COVID-19 messages, bots would spread misinformation through two main techniques.
The first involves content creation, wherein bots start new posts with pictures that validate or mirror existing worldwide trends. Examples include pictures of shopping baskets filled with food, or hoarders emptying supermarket shelves. This generates anxiety and confirms what people are reading from other sources.
The second technique involves content augmentation. In this, bots latch onto official government feeds and news sites to sow discord. They retweet alarming tweets or add false comments and information in a bid to stoke fear and anger among users. It's common to see bots talking about a "frustrating event", or some social injustice faced by their "loved ones".
The example below shows a Twitter post from Queensland Health's official twitter page, followed by comments from accounts named "Sharon" and "Sara" which I have identified as bot accounts. Many real users reading Sara's post would undoubtedly feel a sense of injustice on behalf of her "mum".
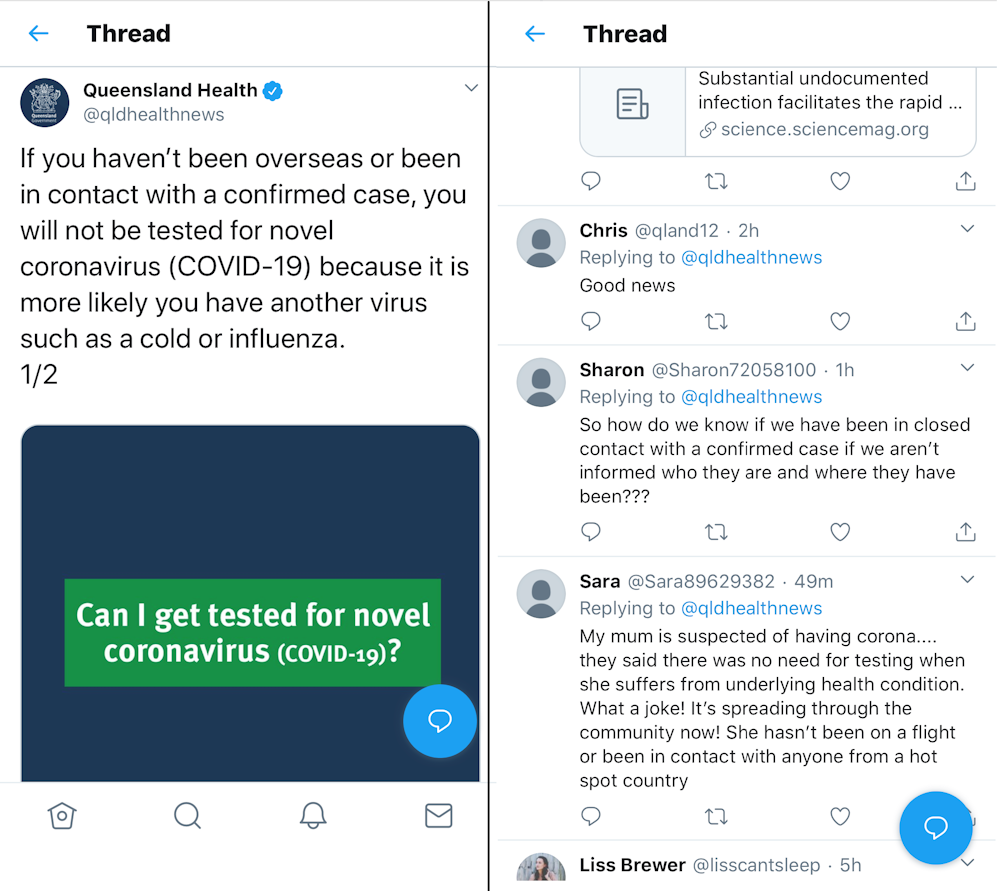
While we can't be 100 percent certain these are bot accounts, many factors point to this very likely being the case. Our ability to accurately identify bots will get better as machine learning algorithms in programs such as Bot Sentinel improve.
How to spot a bot
To learn the characteristics of a bot, let's take a closer look Sharon's and Sara's accounts.
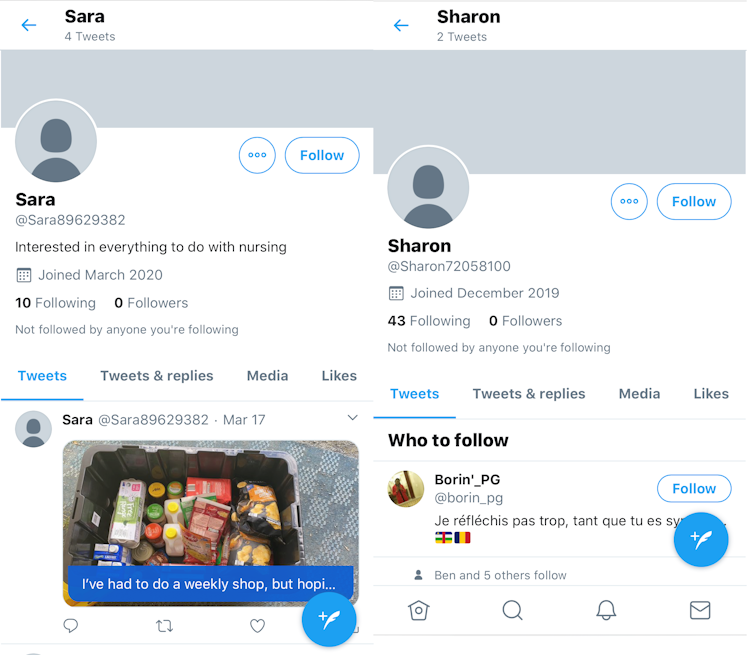
Both profiles lack human uniqueness, and display some telltale signs they may be bots:
-
they have no followers
-
they only recently joined Twitter
-
they have no last names, and have alphanumeric handles (such as Sara89629382)
-
they have only tweeted a few times
-
their posts have one theme: spreading alarmist comments
- they mostly follow news sites, government authorities, or human users who are highly influential in a certain subject (in this case, virology and medicine).
My investigation into Sharon revealed the bot had attempted to exacerbate anger on a news article about the federal government's coronavirus response.
The language: "Health can't wait. Economic (sic) can" indicates a potentially non-native English speaker.
It seems Sharon was trying to stoke the flames of public anger by calling out "bad decisions".
Looking through Sharon's tweets, I discovered Sharon's friend "Mel", another bot with its own programmed agenda.
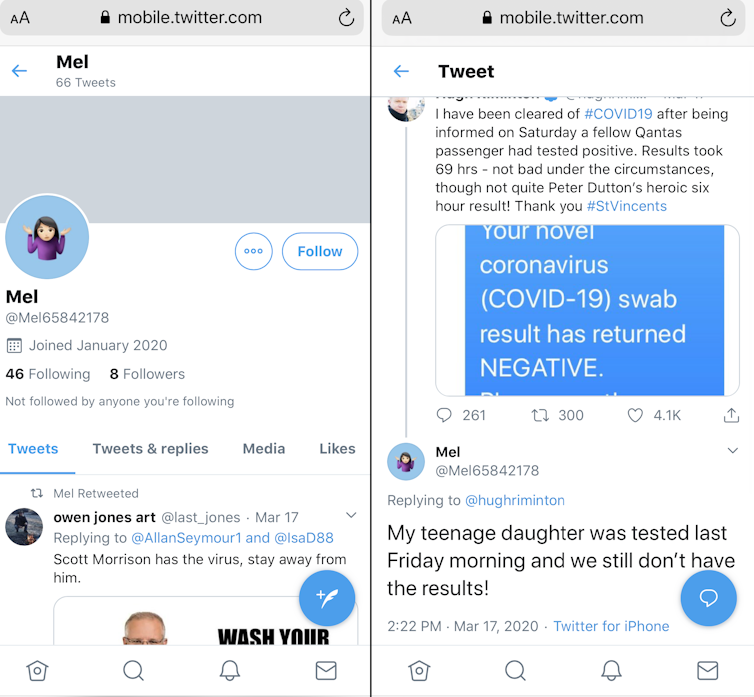
What was concerning was that a human user was engaging with Mel.
You can help tackle misinformation
Currently, it's simply too hard to attribute the true source of bot-driven misinformation campaigns. This can only be achieved with the full cooperation of social media companies.
The motives of a bot campaign can range from creating mischief to exercising geopolitical control. And some researchers still can't agree on what exactly constitutes a "bot".
But one thing is for sure: Australia needs to develop legislation and mechanisms to detect and stop these automated culprits. Organisations running legitimate social media campaigns should dedicate time to using a bot detection tool to weed out and report fake accounts.
And as a social media user in the age of the coronavirus, you can also help by reporting suspicious accounts. The last thing we need is malicious parties making an already worrying crisis worse.
Ryan Ko, Chair Professor and Director of Cyber Security, The University of Queensland.
This article is republished from The Conversation under a Creative Commons license. Read the original article.
