A huge vulnerability in Wi-Fi that fundamentally breaks the security we use to protect our wireless networks has just been exposed.
The exploit, revealed on Monday, breaches a newly found vulnerability in WPA2, the security protocol used to safeguard all modern Wi-Fi networks, and researchers say it could violate virtually any Wi-Fi network previously thought to be secure.
"The attack works against all modern protected Wi-Fi networks," explains the security researcher who discovered the vulnerability, Mathy Vanhoef from Belgium's KU Leuven university.
"The weaknesses are in the Wi-Fi standard itself, and not in individual products or implementations. Therefore, any correct implementation of WPA2 is likely affected."
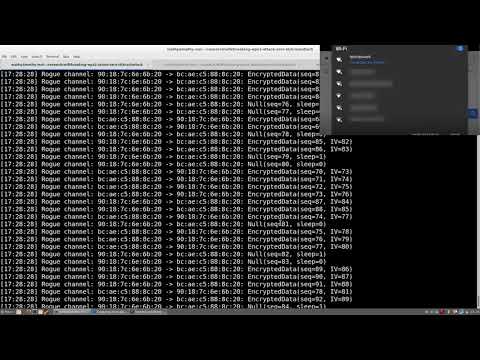
By taking advantage of the vulnerability in what is called a key reinstallation attack (KRACK), a hacker could read information supposed to be encrypted on a Wi-Fi network, intercepting potentially sensitive information like credit card numbers, passwords, photos, and messages.
In the worst case, Vanhoef says, it could be possible for someone to use KRACKs to inject and manipulate data on a compromised Wi-Fi network, hijacking devices to inject ransomware or other malware onto systems.
"Wow. Everyone needs to be afraid," researcher Robert Graham of Errata Security, who wasn't involved with the discovery, wrote in a blog post.
"It means in practice, attackers can decrypt a lot of Wi-Fi traffic, with varying levels of difficulty depending on your precise network setup."
The good news in all this is that the hack can't be executed online: any attacker trying to take advantage of the flaw needs to do so locally, to be within range of the wireless network they're trying to breach.
That's because the attack works by fooling a security layer in WPA2 called the four-way handshake, which determines whether devices seeking to join a Wi-Fi network have the right credentials.
When this happens, the handshake is supposed to generate a fresh encryption key to encrypt all subsequent traffic, but KRACKs manage to fool the network into reusing a previously issued encryption key.
"Essentially, to guarantee security, a key should only be installed and used once," Vanhoef explains.
"Unfortunately, we found this is not guaranteed by the WPA2 protocol. By manipulating cryptographic handshakes, we can abuse this weakness in practice."
In the researchers' testing, the attack worked with varying levels of success against client devices running Apple, Windows, Android, and many other operating systems on compromised networks, and while websites and apps using HTTPS encryption were harder to breach, they weren't always fool-proof.
Fortunately, the code that makes this attack possible hasn't been publicly released – so it's unlikely we'll see a wave of hackers taking advantage of it straight away, because first they'd need to reverse-engineer how it works.
Before that happens, technology companies – who were given fore-warning of the vulnerability – are already busy patching their systems, and some of these patches are already available, which Vanhoef says we should all grab as soon as possible.
"Changing the password of your Wi-Fi network does not prevent (or mitigate) the attack," he explains in an FAQ about the new attack vector.
"Instead, you should make sure all your devices are updated, and you should also update the firmware of your router."
Of great ongoing concern are the many 'Internet of Things' (IoT) devices and appliances now in use that are difficult to update or go unsupported by their manufacturers. These include things like Wi-Fi enabled home security cameras and televisions.
The vulnerability is detailed in a research paper available online, which is due to be presented at the ACM Conference on Computer and Communications Security in Dallas in November.
